Today's CIOs have to deal with the potential challenges of bring your own device (BYOD), mobile applications, software-defined networks (SDN), cloud sprawl, and usability demands, all on a static or shrinking budget.
 As such, organisations are increasingly pursuing enterprise-wide virtualisation and consolidation as a means of improving the cost efficiency, manageability, security, resiliency and flexibility of the business. This is leading to a fundamental transformation in the modern data centre.
As such, organisations are increasingly pursuing enterprise-wide virtualisation and consolidation as a means of improving the cost efficiency, manageability, security, resiliency and flexibility of the business. This is leading to a fundamental transformation in the modern data centre.
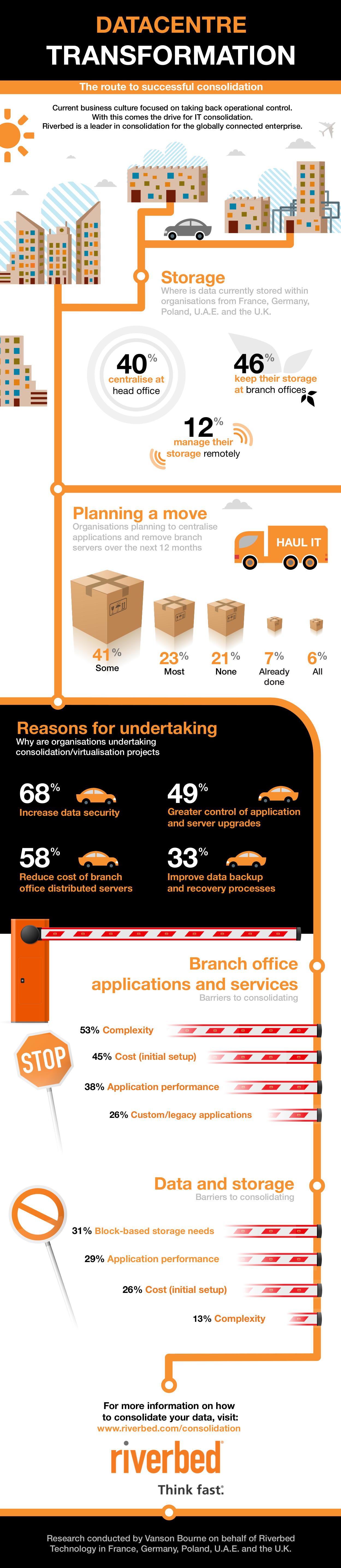
In fact, according to research conducted by Vanson Bourne on behalf of the application performance company, Riverbed Technology, 70% of IT decision makers across Europe and the Middle East are planning consolidation projects during 2013.
Virtualisation is now being extended to production and line-of-business applications. With this broader adoption, customers have begun to look for similar cost savings from broader consolidation efforts. They’re relocating servers from branch offices to consolidated data centres and even consolidating entire data centres and operating IT out of fewer locations, as well as moving certain workloads and data to the cloud.
The study questioned 400 CIOs across France, Germany, the United Arab Emirates, Poland and the United Kingdom. It revealed several major drivers and barriers that CIOs are considering when looking at consolidation.
Drivers
By consolidating and transforming the architecture of underutilised and distributed assets, a business can reduce infrastructure, administration, and power and cooling costs. At the same time it can reduce the volume of hardware to manage, and more easily apply automation policies, improve security, and streamline data protection procedures for disaster recovery and business continuity.
The study found that 68% of those planning a consolidation project report data security as the key driver for their programmes. Reducing the cost of managing distributed servers at the branch office layer (58%) and greater control of application and server upgrades (49%) were also reasons to consolidate. Although these drivers varied in importance across regions, these were all consistently high factors for every business, regardless of location or industry.
Organisations consolidate infrastructure and adopt virtualised deployment paradigms, provision new services and locations, and add scale to existing applications, all with minimal cost overhead and administration.
However, many still harbour concerns about the negative impact that projects like these may have on the business.
Concerns
While transforming the data centre through consolidation holds the potential for improving cost efficiency and mitigating risk, the reality is that IT needs to play a part in supporting productivity and revenue growth. This generally involves supporting users outside the data centre, at the far edges of the network and so post-consolidation performance is a major concern.
The research showed that, of those questioned, over half cited complexity as the biggest obstacle to consolidation efforts. The cost of initial set-up, as well as application performance over the WAN, was also reported as concerns by 45% and 38% of the respondents, respectively.
IT often questions the feasibility of sustaining performance after consolidation, but with the right support and solutions, all these issues can be overcome.
Advice
Consolidation and data centre transformation can fundamentally change a business’s application delivery environment, making it more reliant than ever on the network. As the network becomes critical for centralised applications, changes that used to affect a single location can now impact an entire region.
Another key consideration is that, once applications have been centralised within the data centre and started delivering proven cost savings and efficiencies, there is the potential for performance blind spots amidst the layers of virtualisation in the data centre.
The cost of change is sometimes high, but when an organisation considers the overall savings that can be achieved, the true value of consolidation can be accurately ascertained. This requires an assessment of other recent IT investments and the cost of migrating to cloud services, for instance.
Regardless of whether a business is seeking to improve performance after consolidation or at the start of such a project, performance and simplicity need to be at the heart of the network infrastructure.
In particular, boosting sluggish business applications and slow websites can be dealt with through a combination of WAN optimisation, QoS, and web content optimisation (WCO). Combined, these technologies can help ensure that the increased distance between workers and the data and applications they use don’t slow things down.
Of course, not every application should be moved out of branch offices, but the risks and complications of a distributed application infrastructure can be mitigated. Those few applications that do remain can be virtualised directly on a WAN optimisation appliance and managed remotely with industry standard tools.
Even when reducing the number of data centres, a company’s services and applications will be spread across several locations. Virtual application delivery controllers (ADCs) make it possible to accelerate user and replication traffic between data centres as well as ensure high availability of critical services.
To effectively manage such modernized data centres requires monitoring of the traffic between virtual machines to keep tabs on the performance of virtualised services. With such monitoring tools in place, CIOs can rest assured that their investment is paying dividends and that any potential problems are fixed before they adversely impact the business.
Conclusion
The tools exist to enable a business to successfully consolidate and transform its entire data centre infrastructure. With the right partner, an organisation can easily ensure that network performance is maintained during the consolidation and transformation process. As such, enterprises can successfully and intelligently implement strategic initiatives such as virtualisation, consolidation, cloud computing and disaster recovery, without fear of compromising performance.
The benefits of a well-planned and executed data centre transformation approach can extend beyond merely cost savings, with companies improving the way they mitigate risk and grow. While many organisations have achieved some level of consolidation, beginning with server virtualisation, enterprise-wide consolidation efforts require overcoming greater complexity, latency, and traditional IT organisational silos.
The Vanson Bourne study highlights how CIOs are recognising the importance of centralising technology and data to gain these efficiencies. But some must overcome barriers before they can consolidate their applications or remove branch office servers.
By ensuring that performance challenges are identified, addressed, and managed, organisations can realise greater flexibility in where they locate IT resources. Doing so can mean greater economies of scale, control, and security.












 As such, organisations are increasingly pursuing enterprise-wide virtualisation and consolidation as a means of improving the cost efficiency, manageability, security, resiliency and flexibility of the business. This is leading to a fundamental transformation in the modern data centre.
As such, organisations are increasingly pursuing enterprise-wide virtualisation and consolidation as a means of improving the cost efficiency, manageability, security, resiliency and flexibility of the business. This is leading to a fundamental transformation in the modern data centre.






