Managing the mobile enterprise
BYOD has become the rule, rather than the exception. A recent MobileIron survey revealed that of the 3 000 respondents, a whopping 80% said they regularly use their personal devices – smartphones and tablets – for work purposes.
There can be no doubt that it is no longer a question of if enterprises will implement mobile device management (MDM) policies, but when. And further to this, once the devices are under MDM, businesses will need to address the information sprawl.
Why Wi-Fi will become the next corporate must-have
Wi-Fi is not new. Although it’s hard to track its origins, it’s safe to say Wi-Fi was being used on a large scale for the first time in the late 1990s – which probably qualifies it as being prehistoric in tech terms. But there has been renewed interest in the technology of late, and with good reason.
For one, analysts have predicted that in the next few years, the average people will go from owning two to three Wi-Fi enabled devices (such as a laptop, tablet and smart phone) to seven, or more, if the futurists are correct in assuming that we’ll soon download our emails via our fridges, bedside radios and televisions.
Subscribe content preview
To continue reading: Log-In above or Subscribe now.
Want the full story?

SUBSCRIBE NOW
Get The SA Leader the way you want it
- One Year Digital Subscription - R320
- 10 Issues Print Subscription - R580
- One Year All Access - Just R900 Best Deal!
Print Magazine + Digital Edition + Subscriber-only content on SALeader.co.za
If you are already a subscriber, please Log-In using the Log-In button found on the top right of the site!
CIOs must consolidate to drive data centre transformation
Today's CIOs have to deal with the potential challenges of bring your own device (BYOD), mobile applications, software-defined networks (SDN), cloud sprawl, and usability demands, all on a static or shrinking budget.
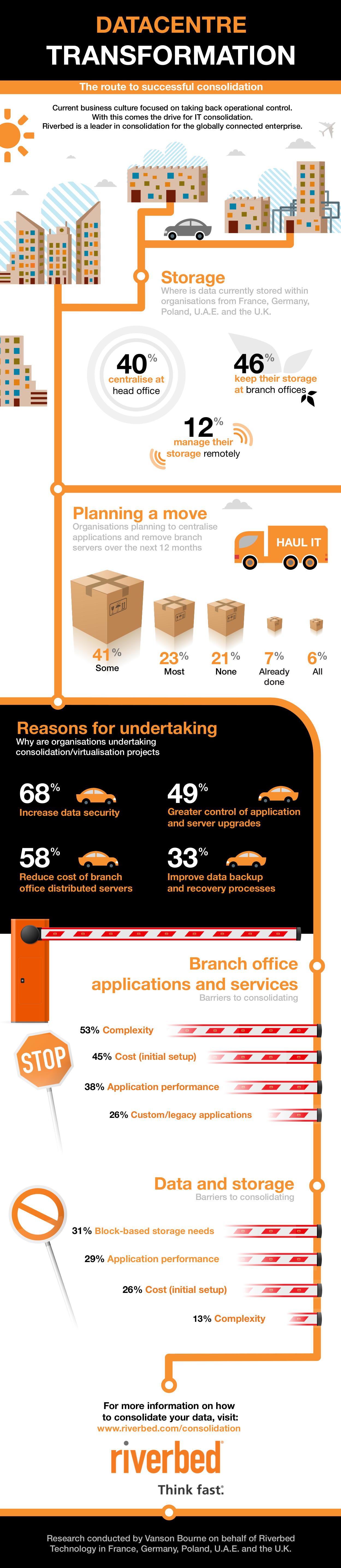 As such, organisations are increasingly pursuing enterprise-wide virtualisation and consolidation as a means of improving the cost efficiency, manageability, security, resiliency and flexibility of the business. This is leading to a fundamental transformation in the modern data centre.
As such, organisations are increasingly pursuing enterprise-wide virtualisation and consolidation as a means of improving the cost efficiency, manageability, security, resiliency and flexibility of the business. This is leading to a fundamental transformation in the modern data centre.
In fact, according to research conducted by Vanson Bourne on behalf of the application performance company, Riverbed Technology, 70% of IT decision makers across Europe and the Middle East are planning consolidation projects during 2013.
Virtualisation is now being extended to production and line-of-business applications. With this broader adoption, customers have begun to look for similar cost savings from broader consolidation efforts. They’re relocating servers from branch offices to consolidated data centres and even consolidating entire data centres and operating IT out of fewer locations, as well as moving certain workloads and data to the cloud.
The study questioned 400 CIOs across France, Germany, the United Arab Emirates, Poland and the United Kingdom. It revealed several major drivers and barriers that CIOs are considering when looking at consolidation.
Drivers
By consolidating and transforming the architecture of underutilised and distributed assets, a business can reduce infrastructure, administration, and power and cooling costs. At the same time it can reduce the volume of hardware to manage, and more easily apply automation policies, improve security, and streamline data protection procedures for disaster recovery and business continuity.
The study found that 68% of those planning a consolidation project report data security as the key driver for their programmes. Reducing the cost of managing distributed servers at the branch office layer (58%) and greater control of application and server upgrades (49%) were also reasons to consolidate. Although these drivers varied in importance across regions, these were all consistently high factors for every business, regardless of location or industry.
Organisations consolidate infrastructure and adopt virtualised deployment paradigms, provision new services and locations, and add scale to existing applications, all with minimal cost overhead and administration.
However, many still harbour concerns about the negative impact that projects like these may have on the business.
Concerns
While transforming the data centre through consolidation holds the potential for improving cost efficiency and mitigating risk, the reality is that IT needs to play a part in supporting productivity and revenue growth. This generally involves supporting users outside the data centre, at the far edges of the network and so post-consolidation performance is a major concern.
The research showed that, of those questioned, over half cited complexity as the biggest obstacle to consolidation efforts. The cost of initial set-up, as well as application performance over the WAN, was also reported as concerns by 45% and 38% of the respondents, respectively.
IT often questions the feasibility of sustaining performance after consolidation, but with the right support and solutions, all these issues can be overcome.
Advice
Consolidation and data centre transformation can fundamentally change a business’s application delivery environment, making it more reliant than ever on the network. As the network becomes critical for centralised applications, changes that used to affect a single location can now impact an entire region.
Another key consideration is that, once applications have been centralised within the data centre and started delivering proven cost savings and efficiencies, there is the potential for performance blind spots amidst the layers of virtualisation in the data centre.
The cost of change is sometimes high, but when an organisation considers the overall savings that can be achieved, the true value of consolidation can be accurately ascertained. This requires an assessment of other recent IT investments and the cost of migrating to cloud services, for instance.
Regardless of whether a business is seeking to improve performance after consolidation or at the start of such a project, performance and simplicity need to be at the heart of the network infrastructure.
In particular, boosting sluggish business applications and slow websites can be dealt with through a combination of WAN optimisation, QoS, and web content optimisation (WCO). Combined, these technologies can help ensure that the increased distance between workers and the data and applications they use don’t slow things down.
Of course, not every application should be moved out of branch offices, but the risks and complications of a distributed application infrastructure can be mitigated. Those few applications that do remain can be virtualised directly on a WAN optimisation appliance and managed remotely with industry standard tools.
Even when reducing the number of data centres, a company’s services and applications will be spread across several locations. Virtual application delivery controllers (ADCs) make it possible to accelerate user and replication traffic between data centres as well as ensure high availability of critical services.
To effectively manage such modernized data centres requires monitoring of the traffic between virtual machines to keep tabs on the performance of virtualised services. With such monitoring tools in place, CIOs can rest assured that their investment is paying dividends and that any potential problems are fixed before they adversely impact the business.
Conclusion
The tools exist to enable a business to successfully consolidate and transform its entire data centre infrastructure. With the right partner, an organisation can easily ensure that network performance is maintained during the consolidation and transformation process. As such, enterprises can successfully and intelligently implement strategic initiatives such as virtualisation, consolidation, cloud computing and disaster recovery, without fear of compromising performance.
The benefits of a well-planned and executed data centre transformation approach can extend beyond merely cost savings, with companies improving the way they mitigate risk and grow. While many organisations have achieved some level of consolidation, beginning with server virtualisation, enterprise-wide consolidation efforts require overcoming greater complexity, latency, and traditional IT organisational silos.
The Vanson Bourne study highlights how CIOs are recognising the importance of centralising technology and data to gain these efficiencies. But some must overcome barriers before they can consolidate their applications or remove branch office servers.
By ensuring that performance challenges are identified, addressed, and managed, organisations can realise greater flexibility in where they locate IT resources. Doing so can mean greater economies of scale, control, and security.
Preparing for the mobile workforce: Bring Your Own Device and beyond
The days where employees were confined to desks in front of a company-owned-and-controlled personal computer are long gone. Workers are increasingly mobile, jetting off to different locations around the country (and the globe), and they no longer keep office hours, preferring to fire off emails and complete tasks on the road and from home.
This was when we first saw the concept of BYOD (or Bring Your Own Device), and with it, Mobile Device Management, enter the market. The premise behind Mobile Device Management was, initially, the need to control the data employees were accessing – mainly for security purposes and to curb the abuse of company Wi-Fi. The first phase of MDM was concerned with restricting information – and with good reason. If a CEO’s IPad, containing the latest pricing strategy, was stolen, the IT department had to be able to remotely shut down the device to prevent a competitor from accessing it. Likewise, if an employee left the company’s service, so would their smartphone - with all the potentially sensitive emails contained on it.
Migrating to ‘Everything over IP’ – can your network handle the pressure?
Converged communications open up a host of opportunities for businesses, and IP is often seen as the ultimate solution to bringing various communication media together. From voice and data to video, security and surveillance, even wireless printing and more, the ‘Everything over IP’ (EoIP) phenomenon has taken the business world by storm. However, migrating all of these various aspects onto an IP network is not as simple as ‘plug and play’. When looking to migrate services onto IP, there are many factors that first need to be considered, including the technical considerations regarding the network. Addressing the network design and architecture up-front is critical to the success of migrating to IP. Data networks become more complex the more services are run over them, and as more services migrate to IP, it becomes increasingly important to ensure uptime and availability. Planning the network correctly, taking into account the needs of each IP service, and choosing the right network partner, are critical in ensuring that EoIP does not backfire on the organisation.
“Collapsing various services onto a single network makes sound business sense; when this is achieved the total cost of ownership of the various services can be lowered. From an end-to-end business perspective, once all services are collapsed onto the IP network, they can all be managed by the IT support organisation on a common platform which allows information to be shared across voice, video, data and so on. This means that content and context rich collaboration are made possible for enhanced productivity,” says Paul Fick, Managing Director of Jasco Enterprise.
IP applications also allow services that were traditionally confined to the office environment to be easily extended to mobile, catering to the ever-growing Bring Your Own Device (BYOD) phenomenon. Applications can be loaded onto tablets and mobile devices, hooking into business systems and providing the same type of services on these devices in remote locations. Services can also be easily provisioned to users, giving them a choice of the device they prefer to work on. This changes the way that users work, enhancing efficiency and productivity. However, in order to cater to these changes, both the network and the services need to adapt.
“When it comes to IP migrations, simply loading a host of previously separate functions onto a single network can have serious negative repercussions for the performance of the network, degrading the quality of all services and making them unusable. This then impacts the productivity of the business and in turn its profitability. For example, adding voice onto a data network without first considering the technical requirements will make voice traffic subject to latency and jitter, and at the same time will hog bandwidth and cause normal data traffic to come to a potential standstill. The quality of the experience is critical in ensuring maximum user adoption, to drive optimum value from investment,” says Andrew Larkins, Systems Engineer at Avaya Networking.
In today’s world it is not possible to retrofit an application onto the traditionally designed network. Deploying new services onto unsuitable network architecture can overload the network, causing bottlenecks in traffic, which in turn can cause the entire network to shut down, resulting in services outages, which pose a serious risk to business. Agility is key and applications should drive the network, to ensure that applications work as expected and the user experience is satisfactory. IT needs to be proactive to deliver agile services in a fast, flexible and secure manner. Business critical applications need to be identified and prioritised on the network, to ensure that consistent levels of service are delivered to these applications regardless of the network load, thus preventing service degradation. This is particularly important with real-time services such as voice and video over IP.
“Voice and video have significant bandwidth requirements. This means that the current network design and capabilities have to be re-examined. Redundancy is also key as services need to continue without affecting quality even if a link goes down. The architecture of the base level network needs to be changed to deliver a stable, always-on network that can be grown and have capacity added as requirements change. The reality is that traditional networks simply are not designed to cater to this loading,” Larkins adds.
For EoIP services, the network must be always-on, scalable and reliable, with active-active forwarding to make the most of all available links, rather than leaving one as a backup. This enables more capacity to be available at all times, and provides automatic failover in the event of a link failure. Networks need to be fit for purpose today and be able to support change and innovation in the future, preventing the necessity to rip and replace the network every time new products or services need to be added.
“The best advice is to look forward to the future. Don’t plan for what you need now, this is the bare minimum and it will change. Organisations require a network that delivers on today’s requirements, with an architecture that can be expanded and scaled to meet future demand. Using open standards technology enables organisations to select a basket of best-of-breed solutions, regardless of vendor, which provides the agility and flexibility needed to match business requirements in an unknown future. And choosing the right service provider to partner with not only removes some of the complexity by giving you access to specialist network design skills, it also ensures that this vision can be brought to life and that networks can continue to add value to the business in years to come,” concludes Fick.
CIOs have to say yes to CEOs

The Bring Your Own Device (BYOD) trend is no longer a ‘trend’. It has happened. Recent predictions from Gartner claim that global PC shipments will decline this year as shipments increase, and there is anecdotal evidence that the majority of employees have accessed company-sensitive information on their personal . Just look at any desk around you in your office and you will spot personal devices scattered among traditional work tools.
Whereas the BYOD phenomenon has previously been associated with a younger generation coming into the workforce, disrupting existing workflows and tools deployed in an office environment, it actually isn’t. In fact, increasingly, it is the C-suite that is driving BYOD.
To leverage the BYOD trend and protect the business, corporates need mobile device management software

The Bring Your Own Device (BYOD) phenomenon, which sees individuals bring their own mobile devices into the workplace, is part of a new business paradigm. It allows business to be conducted remotely, from anywhere, at any time. It drives productivity and competitiveness. But BYOD also poses a significant challenge to organisations, from the large corporate to the Small Medium Enterprise (SME). As we enter the era of mobile computing, a composite security solution that addresses device management, application management, and threat protection has become vital.
More people own mobile devices and use them as personal productivity tools in their private and business lives. To refuse to allow employees to use these tools for work purposes would strategically disadvantage the business. However, if these devices are allowed to connect to the corporate network and access precious business data, the organisation is opening itself up to considerable security risks.
Besides basic protection from viruses or corruption of data, the organisation needs to be in a position to remove or ‘wipe’ corporate data from a device that is lost or stolen, and prevent access of company data by anyone no longer employed by the organisation. There are also privacy issues to consider. The owner of the device is unlikely to want the organisation to be able to access his or her private data or have any control over it. Finding a way to split access and control over personal and business data is thus important.
The answer lies in finding a solution that will assist the business to secure all mobile devices within the organisation, enforce organisational policy and maintain control of the IT environment. The solution should ideally address security of devices, applications and data across personal and corporate devices.
The right management software will ensure the company is positioned for mobility. It should:
- Enable devices for use in corporate environment by providing access to key corporate assets, such as email, calendars, critical mobile applications, documents, and media content.
- Secure devices and data on all devices, including activating appropriate password and access controls, and maintaining separation of corporate data and personal data.
- Manage all devices in the enterprise from a single centralised solution. This includes visibility and control over all phases of device lifecycle with needed administrative and helpdesk options.
The range of tools available to control information and devices is quite large and implementing these tools is becoming a trend throughout business as corporates realise that they are at risk and that people will use their own devices whether they want them to or not.
Enable, secure, manage – the key features
There are some key features to look out for in the solution you select. In terms of enablement, enterprise enrolment will help prevent unauthorised shadow enrolments and provide a standard and automated provisioning process, while self-service activation will reduce IT handholding. A business email feature should include automatic configuration for native and third-party email clients that connect to various mail servers. An in-house enterprise application store will provide the ability to distribute internal or public applications. An enablement solution should also facilitate access to corporate network resources like Wi-Fi and VPN with support for all protocols and authentication methods. A mobile collaboration feature is also vital to makes content available on an end user device of choice.
When it comes to security, ensure the solution’s policy management feature can drive corporate compliance by enabling advanced security settings on devices. All policy options including passwords, remote wipe, and resource and application restrictions should be available and should be able to target specific users, devices, OS’ or groups. Strong authentication, secure email access, data separation and compliance and remediation features are also crucial.
Effective and efficient management of devices is going to be essential. The management features that will make the biggest difference are: centralised management for all mobile devices; integrated management of all the computing devices in the enterprise; management of all enterprise applications through the lifecycle phases with over-the-air (OTA) control; application curation to keep the enterprise mobile ecosystem safe with policy driven blacklisting; dashboards and reports to provide exact details of enterprise mobile assets at all times as well as comprehensive user, device, app, and profile details; and automation of administrative and operational tasks.
The message to corporates is: if you are using mobile devices in your organisation, you are at risk. Leverage the advantage the BYOD trend offers by investing in the software you need to better manage the devices and protect the organisation.
Mobility extends the reach of the business into the market

Mobility enjoys such acceptance in the market that many new enterprise applications are now built for mobile access first and for other devices only as additional channels. In addition, there is large-scale mobile re-engineering of enterprise applications taking place, says Wesley Lynch CEO of Realmdigital.
In short, mobile is the major growth area of the moment; and the success of apps the reason for its popularity.
Unlike Internet-enabled enterprise mobility, apps offer a far more streamlined, tap-once experience. They also depend less on Internet bandwidth to function optimally as the application logic resides mostly on the device itself.
All sorts
Examples of the rise of apps can be seen everywhere in the market, and are of both the consumer-facing and internal varieties. This illustrates the appeal of mobile to companies of all sizes and industries, as well as the rich diversity of apps that have made mobile the next channel of business growth.
The most obvious call for enterprise mobility is from companies with field workers such as sales reps, work-from-home staff or roving employees.
In a sales situation mobility arms agents with more expansive catalogues than physical samples or print outs –facilitating the buying decision, order placements and even transactions.
Beyond sales, opportunity exists for interfacing with enterprise systems in near proximity without the need for desk-bound presence. In this context, depot or warehouse staff can interface with online stock systems and release stock, triggering live status updates of the system with dispatches.
Mobile also offers much more opportunity for self-service, for instance flight check-ins, hotel room bookings or reservations. Airline ground staff can check online seating plans on tablet devices while on-board the aircraft.
Mobility also extends the reach of the enterprise deep into the market, with promise for field service delivery. In this way medical results become available wherever patients or insurance clients find themselves, and can be entered into patient medical records immediately.
The direct, deep and continuous enterprise integration of mobile has increased the pace of doing business and enabled a more distributed layout of computing infrastructure within the enterprise.
Getting ready
With mobility increasing its advance in the enterprise it is important to seriously consider the implications of issues like the bring-your-own-device (BYOD) trend and the demands it places on security and systems management.
BYOD is effectively a convergence between business and personal technology, and it poses significant security problems. BlackBerry 10 has taken a stab at solving the risks with an elegant solution to split personal and business personas. Whether it takes on remains to be seen, but it does make it easier to deactivate enterprise access under certain conditions, such as when an employee resigns.
To make sure security and device management and a range of other mobility issues are seen to, enterprises must adopt a mobile application strategy. Its success will depend on having the right technical architecture and skilled development partnerships to design, develop and deploy the applications.
Will there be an office in ten years’ time?

As technologies change and develop at an ever increasing pace, and mobile workers become more common - where does this leave the conventional office? Will there even be an office in 10 or 20 years?
Security Predictions for 2013

As you round out your 2013 business and IT plans, cybercriminals are resolving to implement increasingly sophisticated threats targeting specific computer systems and organisations big and small.
Last year, businesses saw several serious hacks and breaches. As the arms race between attackers and businesses continues to evolve in 2013, IT departments and security professionals will need to stay on top of the changing tactics and approaches used by criminal hackers in order to protect their organisations.
Here's our take on what security threats and trends we expect to see in 2013:
Threat #1: Social Engineering
This begins with focusing on a tried-and-true blackhat tactic in both the physical and digital worlds – social engineering. Before the computer age, this meant sneaking one's way past a company's defenses with the gift of gab as opposed to a cleverly-worded email. Now social engineering has moved onto social networks, including Facebook and LinkedIn.
Attackers are increasing their use of social engineering, which goes beyond calling targeted employees and trying to trick them into giving up information. In years past, they might call a receptionist and ask to be transferred to a targeted employee so that the call appears to be coming from within the enterprise if caller ID is being used. However, such tactics aren't needed if the details the cybercriminal is looking for are already posted on social networks. After all, social networks are about connecting people, and a convincing-looking profile of a company or person followed by a friend or connection request can be enough to get a social engineering scam rolling.
Threat #2: APTs
Being aware of social engineering is important, of course, because it can be the precursor for a sophisticated attack meant to breach the wall of your organisation. This year saw a number of high-profile attacks (think: Gauss and Flame) targeting both corporations and governments. These attacks are known as Advanced Persistent Threats (APTs). They are highly sophisticated and carefully constructed. The intention behind APT attacks is to gain access to a network and steal information quietly. They take a low-and-slow approach that often makes them difficult to detect, giving them a high likelihood of success.
Additionally, APTs need not always target well-known programs, such as Microsoft Word; they may also target other vectors, such as embedded systems. In a world where a growing number of devices have Internet protocol addresses, building security into these systems has never been more important.
APTs will continue as governments and other well-funded organisations look to cyber-space to conduct their espionage. In fact, APT attacks are running as we speak so look out for those anomalies in your network traffic.
Threat #3: Internal Threats
But some of the most dangerous attacks come from the inside. These attacks can be the most devastating, due to the amount of damage a privileged user can do and the data they can access. In a study funded by the U.S. Department of Homeland Security, the CERT Insider Threat Center at Carnegie Mellon University's Software Engineering Institute and the U.S. Secret Service, researchers found malicious insiders within the financial industry typically get away with their fraud for nearly 32 months before being detected. Trust, as they say, is a precious commodity – but too much trust can leave you vulnerable.
Threat #4: BYOD
The issue of trust comes into play in the mobile world as well, with many businesses struggling to come up with the right mix of technologies and policies to hop aboard the bring-your-own-device (BYOD) trend. Users are increasingly using their devices as they would their PCs, and by doing so are opening themselves up to web-based attacks the same as they would if they were operating a desktop computer.
For attackers, it is likely as well that there will be more attempts to circumvent the app review and detection mechanisms mobile vendors use to guard their app markets. All this means that the flood of iPhones, Google Android phones and other devices making their way into the workplace are opening up another potential gateway for attackers that needs to be secured. Think about it – your smartphone has a camera. It has a microphone. It can record conversations. Add these features to the ability to access your corporate network, and you have the ideal stepladder to climb the walls we are talking about.
Threat #5: Cloud Security
BYOD is not the only thing changing the walls corporations must build around critical data however. There is also this little trend called cloud computing. With more companies putting more information in public cloud services, those services become juicy targets, and can represent a single point of failure for the enterprise. For businesses, this means that security must continue to be an important part of the conversation they have with cloud providers, and the needs of the business should be made clear.
Threat #6: HTML5
Just as the adoption of cloud computing has changed the vulnerability surface, so will the adoption of HTML5. Earlier this year, it was noted at the Black Hat conference, a place where security pros can get a sign of attacks to come, that HTML5's cross-platform support and integration of various technologies opens up new possibilities for attack, such as abusing Web Worker functionality. Even with an increasing amount of attention being paid to HTML5 security, the newness of it means that developers are bound to make mistakes as they use it, and attackers will look to take advantage. So, expect to see a surge in HTML 5 oriented attacks next year, hopefully followed by a gradual decline as security improves over time.
Threat #7: Botnets
But even though the arms race between researchers and attackers favors innovation, expect cybercriminals to spend a lot of time perfecting what they know best, such as making sure their botnets have high availability and are distributed. While the legal takedowns being launched by companies such as Microsoft succeeded in temporarily disrupting spam and malware operations, it is naïve to assume attackers aren’t taking what they have learned from those takedowns and using it to shore up their operations. Botnets are here to stay.
Threat #8: Precision Targeted Malware
Attackers are also learning from the steps researchers are taking to analyse their malware, and techniques were recently demonstrated that can help render analysis ineffective by designing malware that will fail to execute correctly on any environment other than the one originally targeted. Examples of these attacks include Flashback and Gauss. Both have been successful, especially Gauss, at stopping researchers from automated malware analysis. In the coming year, attackers will continue to improve and implement these techniques and make their malware more dedicated so that it only attacks computers with a specific configuration.
One thing is for certain – 2013 is sure to bring an army of exploits and malware through vectors ranging from social networks to mobile devices to employees themselves. As computer and operating system security continues to improve so will cybercriminals’ new techniques to bypass these defenses. All the more reason to make security one resolution we keep.
- Start
- Prev
- 1
- 2
- Next
- End







